Managed Services
This arrangement allows organizations to access expert cybersecurity
services, technologies, and support without the need to build and
maintain an in-house security team fully. Managed cybersecurity services
can be tailored to an organization's specific needs and requirements,
providing a cost-effective and efficient solution to enhance their overall
security posture
Core components of our Managed Services:
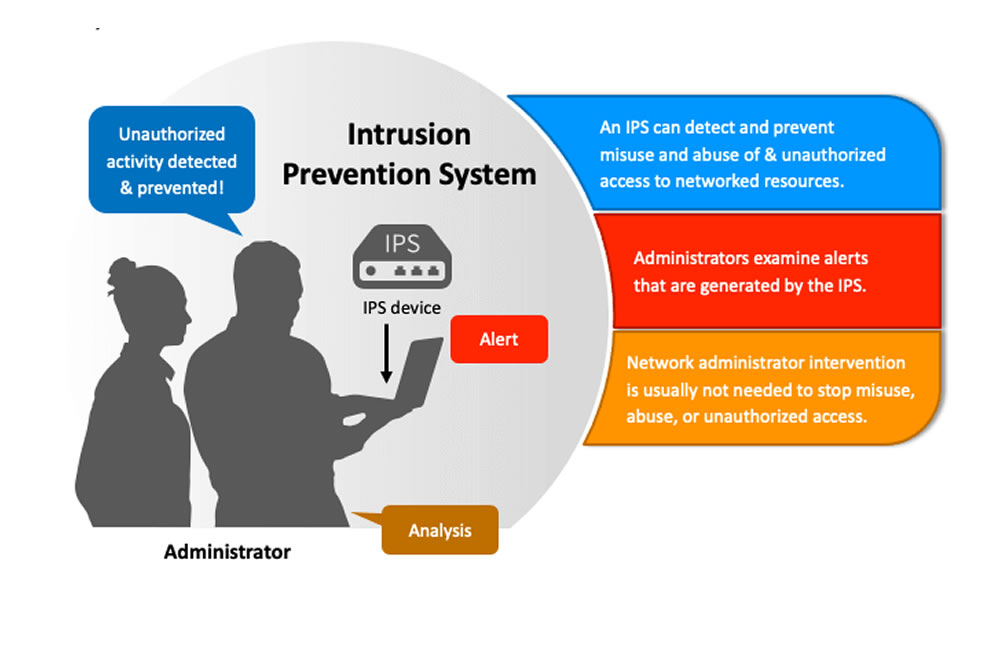
IDS / IPS Management
Intrusion Detection System (IDS): A security tool designed to passively monitor network traffic and detect suspicious activities or potential security breaches.
Intrusion Prevention System (IPS): This goes beyond merely detecting intrusions and takes automated actions to block or mitigate threats.
Management of IDS/IPS:
- Configuration and Tuning:
- Regular rule updates
- Monitoring and Analysis
- Incident Response
- Integration with Security Infrastructure.
Security Patch Management
In Security Patch Management we identify, acquire, test, deploy, and monitor software updates, commonly known as patches, to fix vulnerabilities and address security flaws in computer systems, applications, and network devices.
Our team handles the timely application of security patches and updates for various software and operating systems to address known vulnerabilities and reduce the risk of exploitation.
Importance of Security Patch Management:
- Effective security patch management is crucial for maintaining a robust cybersecurity posture.
- Mitigate Data Breaches: Regular patching minimizes the attack surface and protects sensitive data from unauthorized access.
- Many industry regulations and data protection laws mandate timely patching to safeguard customer data and privacy.

- Enhance Incident Response: Up-to-date systems are better prepared to resist and recover from cyberattacks.
Security Monitoring and Incident Response
We monitor an organization’s network, systems, and applications for potential security threats and anomalies. We use use advanced security information and event management (SIEM) tools and other monitoring technologies to detect suspicious activities, malware, and intrusion attempts.
Security monitoring involves the continuous observation and analysis of an organization’s IT infrastructure, network, applications, and endpoints to identify suspicious or malicious activities.
Incident Response involves detecting, containing, eradicating, and recovering from security breaches and cyberattacks.
Importance of Security Monitoring and Incident Response:
- Early Threat Detection: Security monitoring helps identify threats at their early stages, enabling a proactive response to prevent or minimize damage.
- Timely Incident Resolution: Incident response ensures that security incidents are handled promptly, reducing the dwell time of attackers in the network.

- Continuous Improvement: Incident response analysis leads to valuable insights for improving security measures, closing gaps, and enhancing future incident response capabilities.
- Damage Mitigation: Swift and well-coordinated incident response efforts help limit the impact of security incidents and prevent further escalation.
- Compliance: Effective security monitoring and incident response are often required to meet regulatory and compliance obligations.

